Table Of Contents
- 1Introduction
- 2What Is a Risk Management Framework in Higher Education?
- 3What Does “Risk” Really Mean in a University Setting?
- 4What Are the 5 Key Components of a Risk Management Framework?
- 5The 7-Step Risk Management Framework for Higher Education
- 6Top Risk Management Frameworks Used Across Industries
- 7Common Challenges in Implementing a Risk Management Framework
- 8Common Misconceptions About Risk Management Frameworks
- 9Conclusion
Introduction
Today’s higher education institutions are facing more risks than ever before, especially with the rise of cybersecurity threats. Recent reports show that U.S. colleges and universities have seen over 37 million records exposed in data breaches, with most incidents affecting post-secondary institutions. In 2025 alone, the problem grew even more serious Columbia University reported a breach impacting nearly 870,000 people, and the University of Pennsylvania faced a cyberattack affecting donor and alumni systems, which even led to an FBI investigation.
These incidents highlight the urgent need for universities to have a well-organized system to manage risks. Such a system enables institutions to detect potential problems early, safeguard students and staff, and take action when challenges arise.
What Is a Risk Management Framework in Higher Education?
A risk management framework in higher education is a structured system that helps colleges and universities identify, assess, and address potential risks that could impact students, faculty, and overall institutional operations. By adopting this approach, institutions can proactively manage threats ranging from campus safety and financial challenges to legal compliance and cybersecurity concerns.
Without a clearly defined strategy, universities are vulnerable to preventable incidents such as data breaches, academic misconduct, and operational disruptions. For example, in the first half of 2025, ransomware attacks against U.S. schools, colleges, and universities increased by 23% year-over-year, with roughly 130 confirmed or suspected incidents, highlighting the growing urgency of robust risk management.
An essential component of this framework is understanding the role of the board of directors in compliance and governance. Engaging leadership ensures that proactive measures are effectively implemented, helping institutions safeguard their people, assets, and reputation while maintaining regulatory and ethical standards.
What Does “Risk” Really Mean in a University Setting?
Risk in higher education is often misunderstood. Many assume it only refers to legal trouble or financial loss but in reality, university risk covers anything that can affect how the institution functions, grows, or protects its people. This includes factors that can:
- Interrupt daily academic or administrative operations
- Harm the university’s public image or reputation
- Break legal, policy, or accreditation requirements
- Endanger the physical or emotional well-being of students, faculty, or staff
- Affect long-term financial health, stability, or sustainability
Because universities are complex ecosystems, risks can appear in many forms not just legal or financial. For example:
- Cybersecurity threats: Universities are major targets for phishing, ransomware, and data theft. In fact, 66% of U.S. higher education institutions reported ransomware incidents in 2024, showing how urgently campuses need stronger protective measures.
- Student well-being challenges: Mental health concerns continue to rise. A 2024 survey found that 65% of U.S. college students experienced frequent loneliness, and 29% reported serious psychological distress, underscoring the need for better support systems.
- Political or regulatory pressures: External influences on curriculum decisions, research priorities, or academic freedom can create operational and reputational risks.
- Data breaches: Sensitive information collected during admissions, career services, or research activities can be exposed if systems are not secure.
- Faculty management issues: Challenges such as unclear adjunct contracts, uneven workload distribution, and compliance oversights can impact teaching quality and institutional efficiency.
If your current risk committee agenda doesn’t touch on these emerging challenges, it may be too narrow. A modern university needs a more holistic risk framework one that anticipates threats, strengthens governance, and protects both academic quality and campus safety.
What Are the 5 Key Components of a Risk Management Framework?
A well-defined Risk Management Framework (RMF) is essential in cybersecurity, where relying on assumptions can leave systems exposed. Security cannot be based on hope, it requires a disciplined, proactive approach to uncover potential risks, evaluate their impact, and continuously watch for new vulnerabilities.
An RMF provides this structure. It outlines a systematic process for identifying threats, analyzing their severity, and implementing the right controls to safeguard organizational systems. RMF is built on five essential components, ensuring organizations move from reactive problem-solving to proactive risk prevention.
Risk Identification

The first step in any framework is identifying the risks that could impact an organization. Without knowing where vulnerabilities exist, it’s impossible to address them effectively. These risks may arise from cyberattacks, software flaws, human errors, misconfigurations, or unsafe internal processes.
To identify potential threats, organizations should:
- Maintain a complete inventory of all assets, including devices, systems, and user accounts
- Conduct regular security audits
- Analyze the attack surface to pinpoint weak or exposed entry points
- Review user access controls and track user activity
This stage helps build a clear understanding of what needs protection and where weaknesses may lie. Notably, a 2024 cybersecurity report found that nearly 95% of data breaches stem from human error such as credential misuse, accidental data sharing, or simple mistakes highlighting the importance of thorough risk identification.
Risk Assessment

Once you know what risks could exist, the next step is to measure how serious they are. Risk assessment helps you figure out:
- How likely each risk is to happen
- How much damage it could do if it happens
- Whether the damage would be financial, operational, reputational, or all of these
To evaluate risks effectively, organizations use both quantitative methods (such as estimating costs or potential losses) and qualitative methods (like assigning severity levels). One common tool is the NIST Risk Matrix, which ranks risks from low to high based on their likelihood and impact.
By performing regular assessments such as security audits and penetration tests IT and security teams can detect vulnerabilities early and prioritize the ones that pose the greatest threat.
Risk Mitigation

Risk mitigation focuses on reducing or eliminating risks to acceptable levels. This may involve:
- Implementing new security controls
- Strengthening existing practices
- Adopting industry best practices
- Training employees to avoid risky behavior
For example, a common risk today is unauthorized access to SaaS applications like Salesforce or Zoom. A simple but effective mitigation strategy is enabling Multi-Factor Authentication (MFA) to secure user accounts.
According to Comparitech, education was the fourth-most-targeted sector in the first half of 2025, after business, government, and healthcare. Effective mitigation ensures that if an incident occurs, the damage is limited and recovery is faster.
Risk Monitoring & Incident Response

Cyber risks evolve constantly, which means your defenses must evolve too. Continuous monitoring ensures your mitigation strategies are still effective and identifies new threats early.
Tools like SIEM (Security Information and Event Management) such as Splunk play a crucial role. They analyze logs, detect unusual activity, and alert teams to suspicious behavior in real time.
Monitoring and incident response help organizations:
- Track existing risks
- Detect new vulnerabilities
- Improve security posture based on real data
This ensures your defenses stay strong long after the initial controls are implemented.
Compliance and Governance

Risk management also involves ensuring employees follow established policies and that the organization meets regulatory requirements. RMF is part of the broader GRC Framework, Governance, Risk, and Compliance. Failure to meet compliance standards can lead to severe consequences.
By aligning RMF with compliance frameworks, organizations:
- Avoid legal and financial penalties
- Build customer trust
- Maintain industry-approved security practices
By implementing a structured approach with five essential components, organizations can shift from reacting to problems to preventing them, ensuring stronger protection against evolving cybersecurity threats.
The 7-Step Risk Management Framework for Higher Education
Modern universities operate in a fast-changing environment from digital transformation and cybersecurity threats to enrollment fluctuations and evolving compliance requirements. A structured Risk Management Framework (RMF) helps institutions protect academic quality, financial stability, operational continuity, and reputation.
Step 1: Define What “Risk” Means for Your Institution
Every university has a unique risk profile. A research-intensive STEM institution will face different risks compared to a liberal arts college or a healthcare-focused university.
Start by creating a shared institutional definition of risk and categorizing it into broad themes such as:
- Academic Risk: Program relevance, student performance, accreditation outcomes
- Operational Risk: Facilities reliability, scheduling, transportation, campus safety
- Strategic Risk: Brand reputation, leadership transitions, long-term planning
- Compliance Risk: Accreditation standards, regulatory requirements, audit findings
- Technology & Cyber Risk: System outages, data breaches, LMS failures
- Financial Risk: Fundraising, grants, fee collection, cash flow
- People Risk: Faculty retention, workplace misconduct, student well-being
Assign clear risk owners for each category to ensure accountability.
Step 2: Establish a Diverse and Empowered Risk Committee
A risk committee must represent multiple perspectives because risks do not originate from one area alone. An effective committee typically includes:
- A board or governance representative
- The CFO or senior finance leader
- The CIO or Director of IT
- Head of academic operations or registrar
- Student affairs representative
- External legal or risk expert (recommended)
- Optional: a student representative or observer for transparency
- Use a structured agenda to ensure meaningful discussions.
Step 3: Build and Maintain a Dynamic Risk Register
A risk register should be a living document not a yearly spreadsheet that gets ignored. It must be:
- Organized into clear categories (based on Step 1)
- Updated often (monthly or quarterly)
- Color-coded to show risk levels (red/yellow/green)
- Assigned to specific people with clear deadlines
- Stored digitally so everyone can access and work on it easily
- This keeps risk tracking active, transparent, and efficient.
Step 4: Embed Risk Assessment Into Every Committee’s Work
Risk assessment shouldn’t be handled only by the compliance team. Every important committee in the university should think about risk before making decisions. For example:
- Hostel Committee: Check fire safety, emergency exits, and student safety risks
- Academic Council: Review risks related to enrollment demand, faculty availability, or whether a new program will attract students
- International Relations: Evaluate legal and regulatory risks when signing MoUs or starting exchange programs
Use a simple 3-box checklist for every decision:
- Likelihood | Impact | Mitigation Plan: This approach spreads risk awareness across the whole institution and makes the university stronger and more prepared.
Step 5: Conduct Quarterly Risk Reviews With Board Oversight
Risk management must follow a consistent cycle, not an annual ritual. The risk committee should:
- Meet quarterly with a fixed calendar
- Review the institution’s Top 10 risks
- Track progress on mitigation efforts
- Identify new or emerging risks
- Provide the Board of Governors with a 2-page executive summary
Reports should be concise, visual, and action-oriented—no long, jargon-heavy documents that slow decision-making.
Step 6: Conduct Real-World Risk Drills and Scenario Testing
Being prepared for risks means practicing real situations not just writing about them. Examples of useful drills:
- Cyberattack simulation: Test how quickly IT can detect, isolate, and restore systems.
- Campus safety drills: Fire, evacuation, medical response, or active threat scenarios.
- Accreditation readiness check: Conduct a mock audit to assess documentation quality.
- Communication crisis exercise: Simulate a reputational incident and evaluate response speed.
These drills are important because the threats are real, not theoretical. In the last 20 years, U.S. colleges and universities have faced over 3,100 data breaches, exposing more than 37.6 million records. This shows that security incidents happen often and can affect institutions of every size, making regular testing essential.
Step 7: Make Sure Actions Are Completed After Meetings
Risk management is effective only when decisions turn into real action. Every meeting should end with:
- Clear action points
- A person responsible for each task
- Specific deadlines
- Set dates for follow-up reviews
Many committees struggle at this stage, where discussions occur and minutes are recorded, but progress is often not tracked. Ensuring proper follow-through keeps the risk management process active, accountable, and impactful.
Top Risk Management Frameworks Used Across Industries
Risk management isn’t the same for every organization. Each industry faces its own challenges, so it needs a framework that fits its goals and operations. Here’s an overview of the most common Risk Management Frameworks (RMFs) used today.
NIST Cybersecurity Framework
The NIST framework helps organizations manage cybersecurity risks in a structured way. It was first created for U.S. federal agencies but is now used by companies around the world.
It follows six key steps:
- Categorize – Identify the system and the type of data it handles.
- Select – Choose the right security controls based on the risk level.
- Implement – Put those controls in place and document how they work.
- Assess – Check whether the controls are effective and functioning properly.
- Authorize – A senior leader approves the system to operate after reviewing risks.
- Monitor – Continuously track risks and keep security controls up to date.
NIST also ensures compliance with important regulations like FISMA (Federal Information Security Modernization Act).
ISO 31000
ISO 31000 provides global guidelines on how organizations should approach risk. It applies to all industries and organization sizes.
Its goal is to:
- Make risk management part of daily decision-making
- Create a consistent approach and shared language for managing risk
- Strengthen organizational performance and reduce surprises
In simple terms, ISO 31000 helps leaders make smarter decisions while preventing major disruptions.
COBIT 5
COBIT 5 (Control Objectives for Information and Related Technology) is an IT governance and risk management framework developed by ISACA.
Originally built for financial audits, it now supports all types of organizations.
COBIT 5 helps organizations:
- Link business goals with IT processes
- Manage technology risks more effectively
- Set clear policies, procedures, and controls
- Create backup and communication strategies for risk handling
It offers a structured way to manage IT systems, operations, and security controls from end to end.
FAIR (Factor Analysis of Information Risk)
FAIR is a modern framework that helps organizations understand cybersecurity risks using quantitative (number-based) methods. Unlike older frameworks that rely mostly on judgment or subjective ratings, FAIR allows teams to calculate risk more precisely.
It provides:
- A standard way to collect security data
- Tools to calculate risk levels
- Models to analyze complicated risk scenarios
FAIR helps organizations understand the actual financial impact of cyber threats, making it easier to prioritize the most serious risks.
OCTAVE
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) is a risk management approach focused on protecting important information assets. It evaluates risk by looking at three things:
- Critical assets – Important data or systems needed for operations
- Threats – What could harm those assets
- Vulnerabilities – Weaknesses in processes, technology, or controls
By understanding these areas, organizations can identify what is most at risk and create targeted strategies to protect their information.
Common Challenges in Implementing a Risk Management Framework
Many organizations that focus on security often assume their risk controls are fully established. In reality, they frequently face challenges such as employee resistance, limited resources, and constantly evolving cyber threats. Below are three of the most common obstacles, along with practical solutions to address them.
Resistance to Change
One of the main challenges in implementing a Risk Management Framework (RMF) is employee resistance. New security processes can feel disruptive, especially when they change established workflows.
How to Address It:
- Explain the importance of RMF and how it protects organizational data, operations, and individual roles.
- Involve staff in the process from the beginning to foster ownership and reduce resistance.
- Offer practical sessions that help employees understand and apply new security processes.
- Highlight the advantages of enhanced security and how it contributes to organizational and personal safety.
Human factors remain a critical concern in cybersecurity. A 2024 report found that 74% of CISOs consider human error the top cybersecurity risk, emphasizing that people-related challenges are a primary focus for security leaders.
Limited Resources and Budget Constraints
Many small and mid-sized organizations face tight budgets and lean IT teams. Establishing a comprehensive risk management function or purchasing advanced security tools can seem daunting.
How to Address It:
- Focus first on the most important areas, such as customer data, financial systems, and core applications, instead of trying to implement everything at once.
- Use automated tools for tasks like risk assessments, compliance reporting, and monitoring to reduce manual workload and maximize efficiency.
- According to a Proofpoint report, 87% of global CISOs are adopting AI-powered solutions to reduce human error and address advanced, human-centered cyber threats.

- Leverage solutions like EDMO Document Intelligence to automate document workflows, track compliance, and maintain real-time visibility, helping teams manage risks efficiently even with limited resources.
This approach allows organizations to effectively manage risks while staying within budget and resource limitations.
Keeping Up With Evolving Cyber Threats
The cybersecurity environment is always evolving. As attackers create new techniques, rules and regulations change, and older security measures become less effective. If an organization doesn’t regularly update its approach, it can quickly fall behind and become exposed to new threats.
How to Address It:
Adopt a continuous monitoring approach to ensure the RMF remains relevant. This includes:
- Regularly updating policies and procedures to address emerging threats and regulatory changes.
- Leveraging advanced threat intelligence tools that provide real-time insights into vulnerabilities and attack patterns.
- Conducting periodic audits to identify gaps and strengthen controls.
- Providing ongoing cybersecurity training for employees, keeping them informed of current threats and best practices.
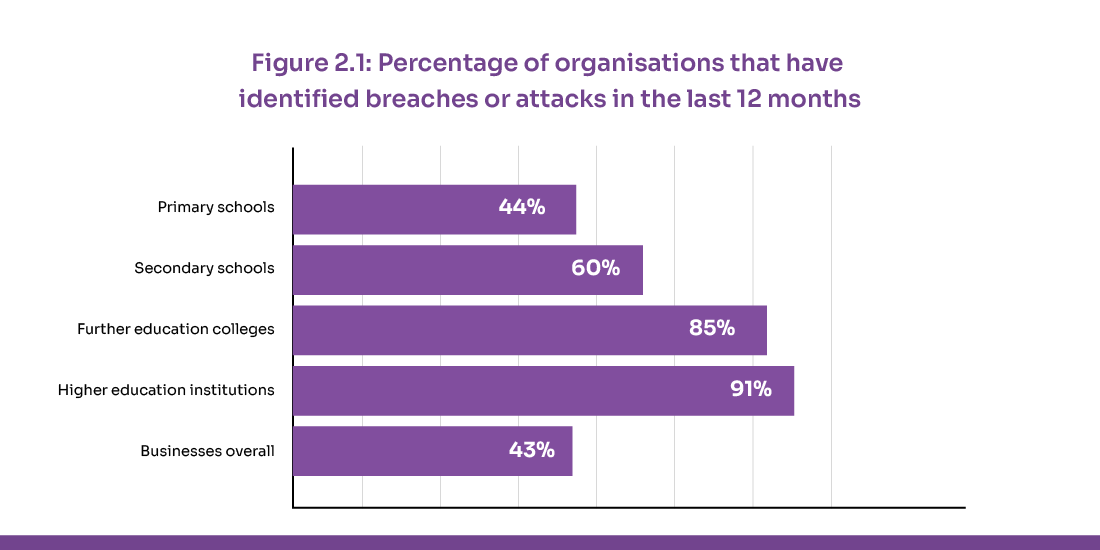
Source: Gov.uk
The risks are tangible and widespread. For example, a 2025 survey reported that 91% of higher-education institutions experienced at least one cyberattack in the past year, underscoring that no organization is immune to evolving cyber threats.
Building a structured approach to managing risks can seem intimidating, but many myths make the process appear more complicated than it actually is.
Common Misconceptions About Risk Management Frameworks
Adopting a new framework can feel overwhelming, especially when misconceptions make the process seem more complicated than it really is. Let’s break down some common myths about risk management frameworks and clarify why they are far more practical, flexible, and valuable than many assume.
Myth 1: “Risk Management Is Only for Large Organizations”
Many people believe that only big universities or well-funded institutions need formal risk processes. But the truth is, every institution big or small faces risks and can benefit from having a clear, organized way to manage them.
- According to a 2025 survey, 71% of U.S. colleges and universities identified enrollment trends as a top institutional risk, demonstrating that both large and small institutions actively recognize and manage critical risks.
- Risk management is similar to financial planning: a multinational corporation may have a dedicated team handling complex portfolios, while a small business owner manages finances independently.
Why It Matters:
- A properly tailored RMF helps identify and mitigate potential threats, regardless of the organization’s size.
- For smaller or more agile institutions, effective risk management can create a safer environment for innovation and growth, supporting strategic initiatives without overextending resources.
Myth 2: “One-Time Implementation Is Enough”
A common misconception is that implementing a Risk Management Framework (RMF) is a one-off task. In reality, effective risk management is an ongoing process that requires continuous review and updates.
- The business and technology environment is constantly evolving, and so are the risks. Using an RMF without regular updates is like navigating a city with a five-year-old map—new roads, construction, and detours make it outdated.
- In 2025 alone, there were 130 confirmed or suspected ransomware attacks targeting schools, colleges, and universities, with the average ransom demand reaching approximately US $556,000.
- Additionally, a 2025 survey found that 57% of U.S. universities now consider AI a strategic priority, yet fewer than 40% have formal policies to govern its use.
Why It Matters:
- Regularly revisiting and updating your RMF ensures it remains relevant and effective against emerging threats.
Myth 3: “It’s Too Complex for Our Organization”
Another misconception is that RMFs are overly complex and require specialized expertise. The truth is, RMFs are scalable and can be adapted to any organization’s size, resources, and complexity.
- A framework can start simple and gradually incorporate more sophisticated controls as your organization grows in experience and resources.
- Even a basic RMF provides significant benefits and is far more effective than having no structured approach at all.
Why It Matters:
- A simplified RMF makes risk management practical and manageable, helping organizations stay secure without feeling overwhelmed.
Conclusion
As risks continue to grow in higher education from cyberattacks to compliance issues institutions need a clear and proactive approach. Having a structured system to identify, assess, and manage risks helps protect students, staff, and data, while also making the institution stronger and more resilient.
By following a step-by-step process, universities can create a safer and more reliable environment for learning, research, and innovation. With the right strategy, institutions are better prepared to handle new threats, make smart decisions, and ensure long-term stability and success.









No comments yet. Be the first to comment!
Leave a Comment